Every year, there is a rise in the number of businesses moving the cloud. At the same time, the number of cyberattacks is also on the rise. A 2021 survey shows that in 12 months, the average cost of compromised cloud accounts reached $6.2 million. As the number of devices and access to the new technology grows, most organizations find it challenging to monitor them, leaving them prone to cyberattacks.
Although cloud vendors invest heavily to secure their products, ensuring security and compliance is a shared responsibility between the cloud service provider and the customer. The Shared Responsibility Model is one such security framework that dictates the shared accountability between cloud service providers and their users.
Check out this infographic on Shared Responsibility Model to learn more about how you can keep your applications and workloads secure when migrating to the cloud.
What is the Shared Responsibility Model?
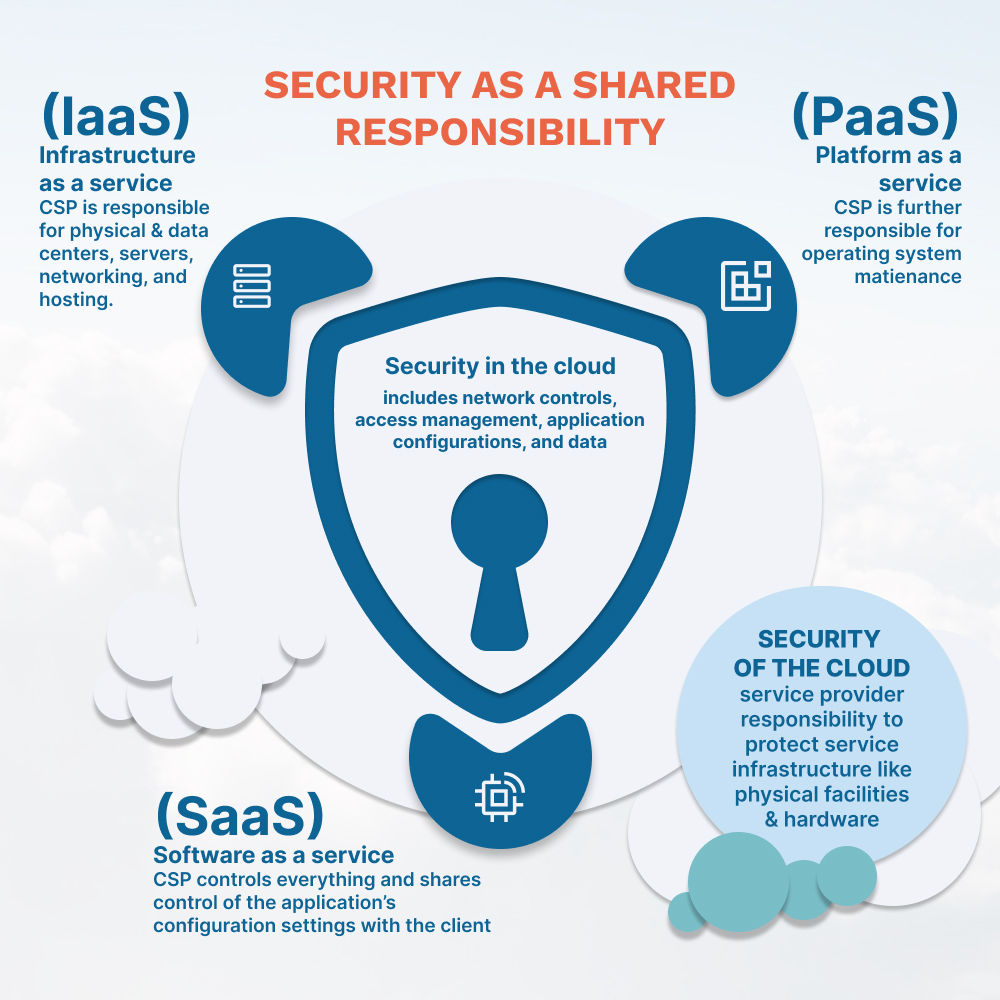
- The Shared Responsibility Model defines the responsibilities of both the cloud service provider, or CSP, and the client company in securing data, applications, and infrastructure hosted on the cloud.
- A report by Gartner predicts that 99% of cloud security failures will be on the client-side through 2025. At the same time, according to Jay Heiser of Gartner says, “ Exaggerated fears can result in lost opportunity and inappropriate spending.”
- The rate can be tackled with policies on cloud ownership, responsibility, and risk acceptance. Security practitioners for the company must understand what they are responsible for in the SRM.
The Two Aspects of Cloud Security
- “Security of the Cloud”: the responsibility of the service provider to protect the infrastructure offered as part of the service, including physical facilities, utilities, cables, hardware, etc.
- “Security in the Cloud”: the security at the client end that includes network controls, access management, application configurations, and data.
Shared Responsibility Across the Three Service Models of Cloud
- Infrastructure as a service (IaaS): CSP is responsible for the physical data center, networking, and servers/hosting.
- Platform as a service (Paas): CSP is further responsible for maintaining operating systems.
- Software as a service (SaaS): The CSP controls everything and shares control of the application’s configuration settings with the client.
Key Considerations
- Inventorying service usage: Keep track of who is accessing what information or applications
- Compliance with regulatory frameworks: You must ensure that the services you are using comply with the applicable regulatory frameworks
- Understanding contractual/legal aspects: You must thoroughly understand contractual agreements such as CSP service level agreements.
Takeaways
- Cloud security is a shared responsibility.
- The various responsibilities are distributed according to the service models.
- The shared responsibility model implies pro-active documentation and practices to avoid incidents of cyber-attacks
- You can employ third-party security tools on top of the CSP’s native security tools to enhance the protection.
Conclusion
While migrating to the cloud brings significant cost savings, businesses must also ensure that their sensitive data on the cloud is secure. Despite the fact that cloud vendors take every step to keep their infrastructure secure, ensuring that the cloud environment remains secure is a shared responsibility with customers.
SOURCES
https://docs.microsoft.com/en-us/azure/security/fundamentals/shared-responsibility
https://www.paloaltonetworks.com/cyberpedia/cloud-security-is-a-shared-responsibility
https://aws.amazon.com/compliance/shared-responsibility-model/
https://www.cisecurity.org/insights/blog/shared-responsibility-cloud-security-what-you-need-to-know
Recent Posts
March, 2022
Cloud computing facilitates storing or accessing applications, programs, and data over the internet instead of directly accessing them on your computer hard drive. The cloud icon often used to picture the Internet in flowcharts and diagrams inspired the term cloud computing.
Most of us would have already used several cloud computing services in our personal or professional lives. For example, document sharing services like Google Docs, Microsoft 365, and Dropbox; social networking sites like Facebook and Twitter; telecommunications applications like Skype; online streaming services like Netflix; Machine Learning (ML), Big Data analysis and Internet of Things (IoT) are all popular cloud computing services.
The worldwide cloud computing market is valued at roughly $369 billion in 2021 and is speculated to increase in size at a Compound Annual Growth Rate (CAGR) of nearly 16% from 2022 to 2030.
There are several types of cloud services. Some of the most popular ones are Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS). These cloud computing services can be set up in public or private cloud computing ecosystems.
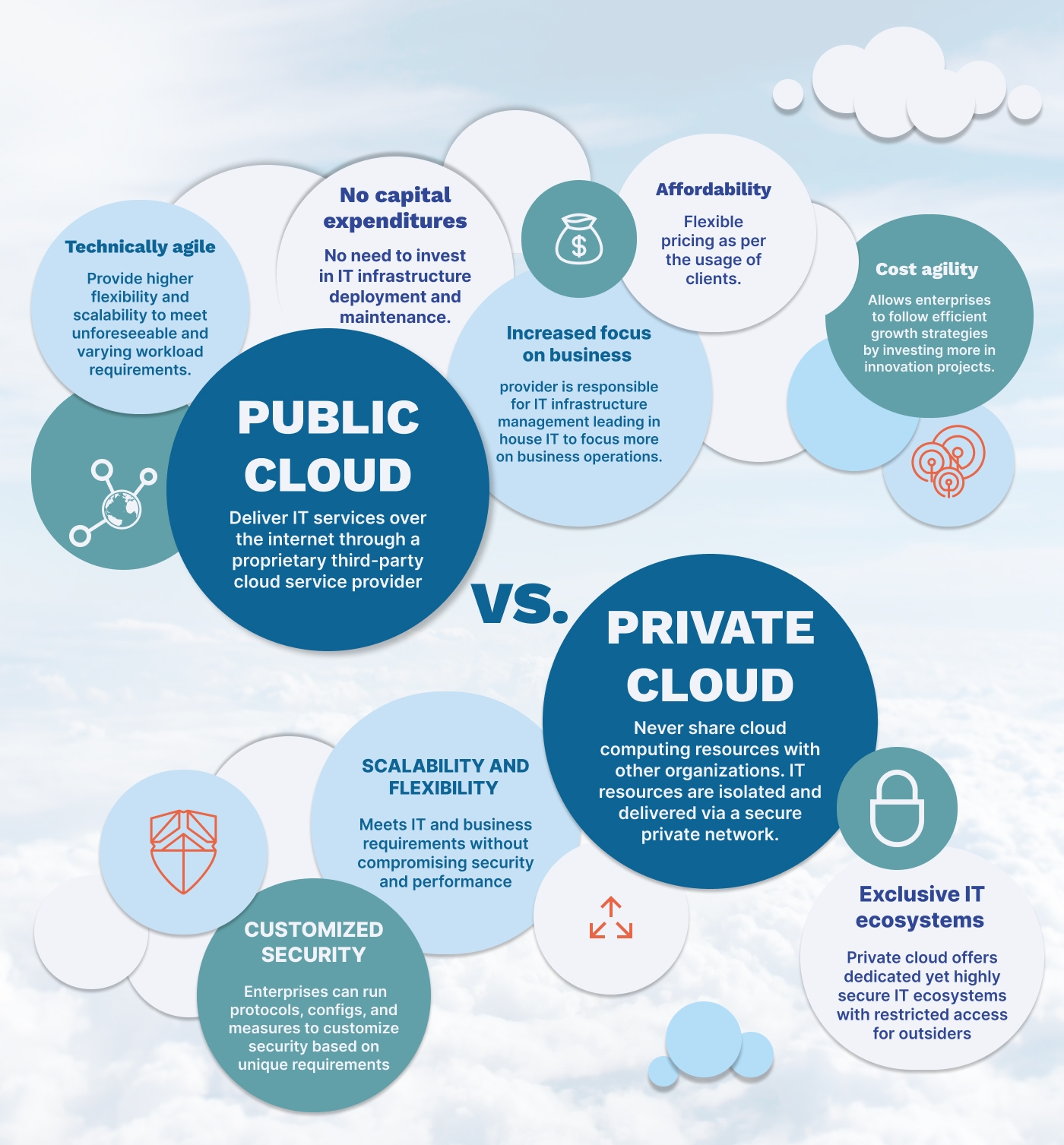
The Public Cloud
Public clouds – the most popular cloud model – deliver Information Technology (IT) services like storage and servers over the internet by a proprietary third-party cloud service provider. Every hardware, software, and other supporting infrastructure in a public cloud is owned and operated by the cloud services provider. The user can access these services by managing an account using a web browser.
The unique features of public cloud services include:
- Higher levels of scalability and elasticity
- A lower subscription fee based on tiered pricing
Public cloud computing services are offered as free, freemium, or premium models, in which you are charged based on the IT resources you use. The public cloud computing services may range from standard IT services like email, applications, and storage to the enterprise-grade Operating System (OS) platform or IT infrastructure used for software development and testing.
The third-party cloud computing services provider is responsible for developing, operating, and maintaining the pool of IT resources shared between multiple users from across the network.
Public Cloud Use Cases
The public cloud computing services are best suited for the following business ecosystems.
- An enterprise with predictable IT needs like communication or collaboration services for a specific number of users.
- An enterprise in need of applications and services necessary to perform specific IT and business operations
- A business that requires additional IT resources to meet varying demands and requirements
- To meet software development and testing requirements
Benefits of Public Cloud
- No capital expenditures (CapEx): An enterprise doesn’t need to invest in IT infrastructure deployment and maintenance.
- Technically agile: It provides higher flexibility and scalability to meet unforeseeable yet varying workload requirements.
- Increased focus on business: The cloud services provider is responsible for IT infrastructure management. So, the complexities and requirements of in-house IT expertise are minimized, bringing more focus on business operations.
- Affordability: Flexible pricing as per the usage of clients.
- Cost agility: It allows enterprises to follow efficient growth strategies by investing more in innovation projects.
Pitfalls of Public Cloud
- Lesser control over cost: In higher usage, the Total Cost of Ownership (TCO) can also increase accordingly.
- Lower cybersecurity levels: Public cloud is the least secure cloud computing service, and it is not suitable for information-sensitive and mission-critical IT operations.
- Lower technical control: Lower visibility and control of the public cloud IT infrastructure may not meet your compliance needs.
The Private Cloud
The private cloud is a dedicated yet ‘private’ cloud computing service. An enterprise that uses a private cloud never shares its cloud computing resources with any other organization. Instead, the IT resources are isolated and delivered via a secure private network. The private cloud can be customized as per a business organization’s specific business and security needs.
Private Cloud Use Cases
The private cloud is suitable for:
- Government agencies and highly regulated industries
- An enterprise that uses sensitive data
- Businesses that require solid control and security over their workloads and IT infrastructure
- Enterprises that need advanced data center technologies for efficient and cost-effective business operations.
Benefits of Private Cloud
- Exclusive IT ecosystems: Private cloud offers dedicated yet highly secure IT ecosystems with restricted access for outsiders.
- Customized cybersecurity: Enterprises can run protocols, configurations, and measures to customize security based on unique workload requirements.
- Scalability and flexibility: Higher scalability, flexibility, and efficiency to meet unforeseeable requirements of ever-changing IT and business environments without compromising performance and security.
Pitfalls of Private Cloud
- Higher Cost: The private cloud is expensive compared to public cloud services.
- Immobility: Due to higher security measures, users with mobile devices have limited access to private cloud services.
- Lower Scalability: The private cloud infrastructure may not offer higher scalability if the cloud data center is based on on-premise IT resources.
Recent Posts
March, 2022
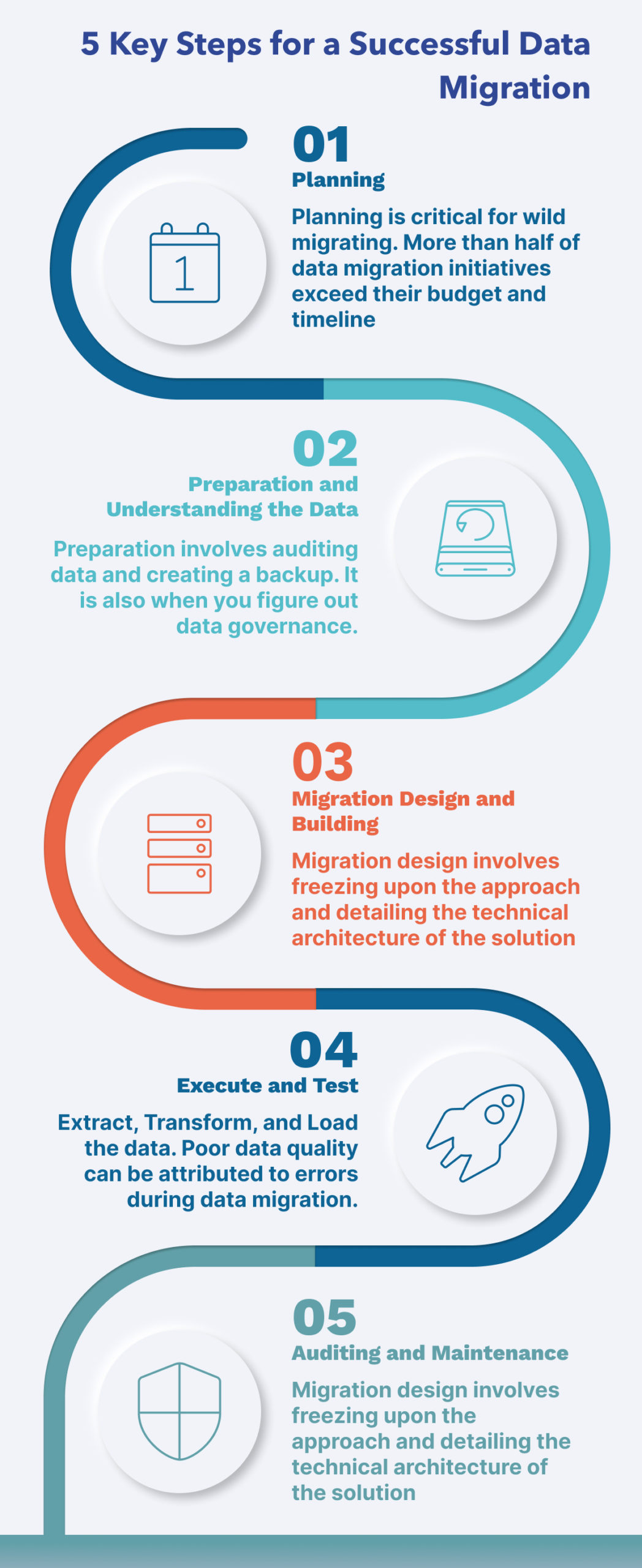
You could be migrating storage information or databases from small to large sizes. In any case, you need to plan ahead in data migration, execute with the right strategy, and ensure data accuracy.
Let us walk through the process in this step-by-step breakdown.
-
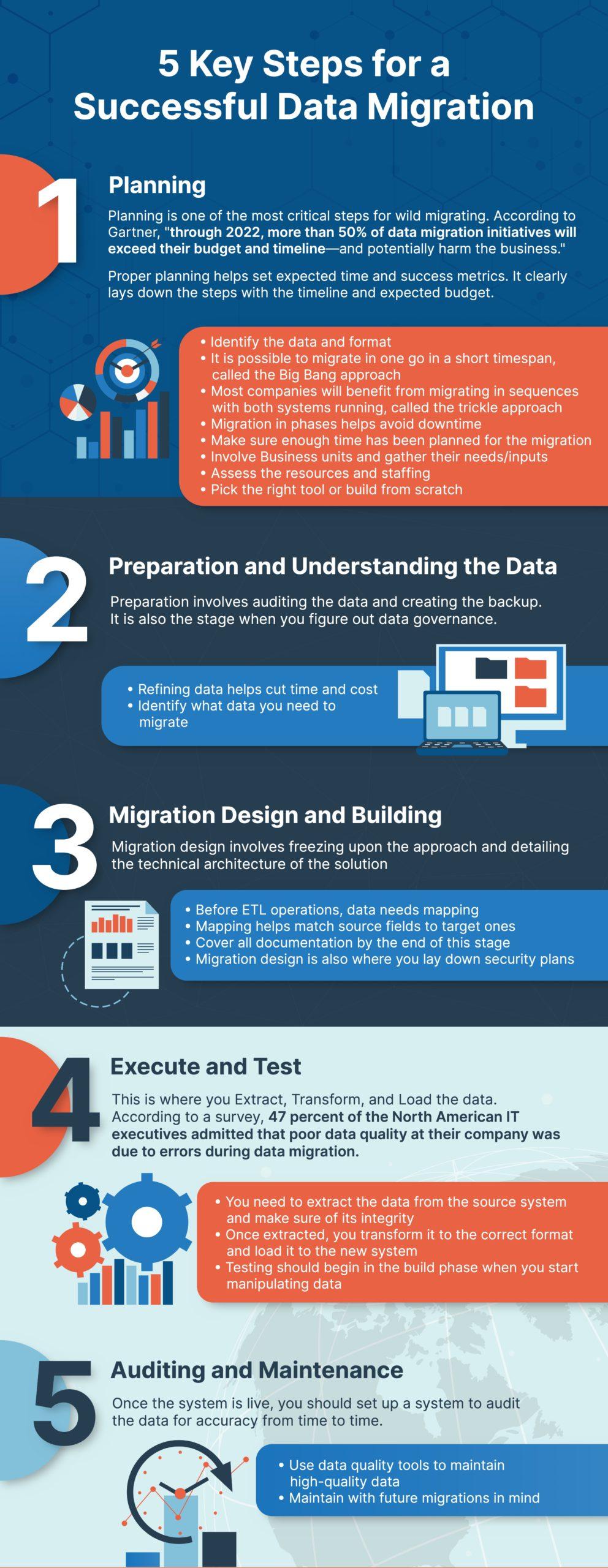
Planning
Planning is one of the most critical steps for wild migrating. According to Gartner, “through 2022, more than 50% of data migration initiatives will exceed their budget and timeline—and potentially harm the business.”
Proper planning helps set expected time and success metrics. It clearly lays down the steps with the timeline and expected budget.
- Identify the data and format
- It is possible to migrate in one go in a short timespan, called the Big Bang approach
- Most companies will benefit from migrating in sequences with both systems running, called the trickle approach
- Migration in phases helps avoid downtime
- Make sure enough time has been planned for the migration
- Involve Business units and gather their needs/inputs
- Assess the resources and staffing
- Pick the right tool or build from scratch
-
Preparation and Understanding the Data
Preparation involves auditing the data and creating the backup. It is also the stage when you figure out data governance.
- Refining data helps cut time and cost
- Identify what data you need to migrate
-
Migration Design and Building
Migration design involves freezing upon the approach and detailing the technical architecture of the solution
- Before ETL operations, data needs mapping
- Mapping helps match source fields to target ones
- Cover all documentation by the end of this stage
- Migration design is also where you lay down security plans
-
Execute and Test
This is where you Extract, Transform, and Load the data. According to a survey, 47 percent of the North American IT executives admitted that poor data quality at their company was due to errors during data migration.
- You need to extract the data from the source system and make sure of its integrity
- Once extracted, you transform it to the correct format and load it to the new system
- Testing should begin in the build phase when you start manipulating data
-
Auditing and Maintenance
Once the system is live, you should set up a system to audit the data for accuracy from time to time.
- Use data quality tools to maintain high-quality data
- Maintain with future migrations in mind
Data migration is essential when moving to a cloud-centric environment, which is the current trend. Use data migration to get better performance and competitive advantage.
 SOURCES
SOURCES
https://www.bloorresearch.com/technology/data-movement/#emergingtrends
https://www.oracle.com/technetwork/middleware/oedq/successful-data-migration-wp-1555708.pdf
https://www.talend.com/resources/understanding-data-migration-strategies-best-practices/
https://easternpeak.com/blog/7-key-steps-to-perform-a-successful-data-migration/
https://zipreporting.com/en/data-migration/data-migration-process.html
Recent Posts
March, 2022


 SOURCES
SOURCES