The transformation seen in the cloud for financial services has been nothing short of phenomenal especially during the last few years. Then when the pandemic hit, cloud services were in such demand that many financial institutions were impressed with the ease with which their workforce was easily able to transition to remote office work without too many hiccups as an “underlying digital transformation” had begun years ago to help modernize the workplace.
Beyond the obvious Zoom meetings and collaboration tools flooding the market both before and during the pandemic, it was obvious that a trend towards greater reliance on cloud basedservices was underway in the financial world. These shifts were seen as advantages from the past where the big banks were at first reluctant to take the big leap into cloud, whereas now are being public about their adoption of cloud tech. For many big banks, it was a question of staying competitive and relevant in an area that has long been reluctant to any rapid changes in procedures and manners of handling sensitive customer data. The notion of putting sensitive information into a product that few were familiar with until cloud technology spread through the workforce at all levels made many in the C-suite nervous about security protocols and relied heavily on outside consultants and their internal IT security experts to educate, innovate, and manage the process of ensuring data security and privacy at all costs.
Flexibility Allows Scalability
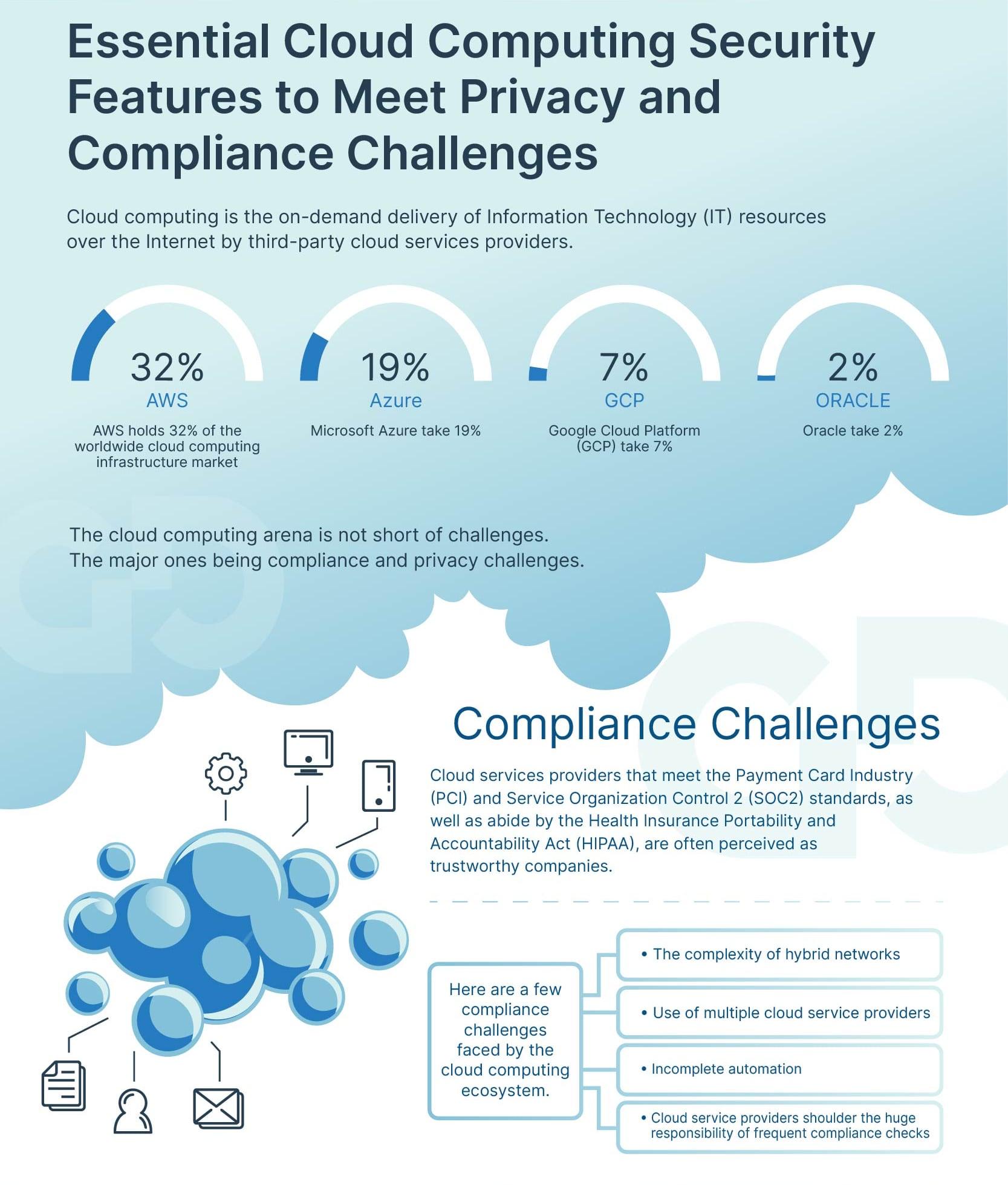
The times have changed. Enterprise migration into the cloud has made it easier for large and small fintech firms as well as large traditional banks and other finserv institutions to streamline their workflows and innovate faster and in more seamless ways than before. The implications have been nothing short of impressive and in some cases mind boggling. According to Bloomberg, cloud adoption though in it’s early stages is still happening at a fairly robust rate, as 22% of ALL applications are now run on the cloud with more room to grow. According to the IDG Cloud Computing Study (2020), almost 55% of all financial firms and fintech companies are using multiple public clouds.
Fintechs are often rapidly growing platforms. This means they need an infrastructure that can grow with them and not put up unnecessary barriers or create challenges where there needn’t be any. Cloud technology provides the agility to scale relatively easily while saving on on-premises technology infrastructure, which can be more costly to upgrade. Even for traditional banking structures, the cloud platform delivers the capacity to adapt to branch closures while still providing services to as many people as possible. Moving infrastructure to the cloud measures accessibility, flexibility, and scalability for both fintechs and financial giants.
Another stunning figure is that these companies are dedicating 32% of their IT budgets to cloud migration and other cloud related services. It’s easy to see why this sector is finally running along with other industries in being cloud savvy. Moving to the cloud is allowing for more agile applications, more growth, more scalability and along with all that comes innovation.
Innovation
As mentioned in Bloomberg: Increasingly, businesses are developing innovations that wouldn’t necessarily be possible without the cloud: enabling fintechs to get up and running faster and offer individualized services, which has encouraged a revolution in financial services. This shift is undoubtedly broadening the competitive landscape. Many also say that agility is a major reason for seeing movement to the cloud.
Companies can now harness the resources as needed which allows for more development of applications in quicker more nimble and secure environments. As of late, even large banks are moving at a more rapid pace and sharing data like startups in the industry. Since cloud technology offers companies more options with less risk, as well as more experimentation and invention on behalf of customers, it’s possible to explore alternative data sets and spend time and capital on proprietary analysis.
New Security & Privacy Options
Despite early concerns about security and data protection, the cloud has proved reasonably secure if the right measures are taken. Zero-trust verification and encrypted data have increased cloud security in recent years. When used alongside measures such as employee education and access control, among others, the cloud proves itself no riskier than traditional IT infrastructure setups. For fintech providers, no doubt, security is at the forefront of their minds when adopting new technology, and it’s vital they ensure their systems have adequate measures in place. The financial services sector has a responsibility to safeguard the data of its customers and the cloud is enhancing the way financial businesses do this. From data encryption to zero trust verification and access control, many of the risks that traditional on-premises IT infrastructures present are being mitigated through cloud computing in financial services.
According to Bloomberg “As migrating data, storing data, and using additional services like machine learning on the cloud becomes more ubiquitous, there’s a clear and demonstrated need for organizational oversight. Many of the tools needed to keep data confidential and secure are readily available within public clouds, enabling firms to take advantage of better security than what is available on their local servers, if they plan appropriately.”

Data Management
Acquiring and working with data is a top priority, from onboarding and identity verification processes to account management, balance, checking, analyzing spending habits, etc. Data is key. Companies can use cloud technology to gather and store large quantities of data securely and make it accessible at any time. That means there’s no need to wait for an IT specialist to clock in to access vital information, providing an employee has the correct credentials. This can be done from anywhere at any time and often automatically.
Best Practices For Cloud Adoption In Finance
Working with more documentation and creating, storing and sharing a great amount of financial information make cloud adoption in banking and fintech specific. Here are the things to consider:
- Encryption and access control: Discuss encryption policies and procedures with your provider to select the technically feasible ones and properly protect the financial data you transmit.
- Compliance: Finance executives need to ask providers to demonstrate compliance certificates of the cloud service.
- Data segregation and data management: Cloud services thrive on shared resources, though financial institutions may require a combo of shared resource benefits with the increased security reached by data segregation.
- Disaster recovery plan: Reputable service providers always have it in place, and it’s important to obtain a detailed disaster recovery plan and ensure your digital infrastructure allows all that.

How GoDgtl Partners with the major cloud providers AWS, Azure, and Google
GoDgtl brings a team of experienced cloud experts who work directly with AWS, Azure, and Google to bring value and real solutions for your cloud projects. With direct access to resources and in house cloud consulting talent, GoDgtl is ready to guide you through your financial/fintech cloud journey regardless of where you are on that path. Whether it’s more knowledge-based information on cloud topics such as security, or governance and compliance or basic cloud migration aspects or even if an assessment is needed, GoDgtl can provide a roadmap for your path to project completion and success.
Sources:
https://www.pwc.com/us/en/industries/financial-services/cloud.html
https://www.telehouse.net/blog/the-impact-of-cloud-computing-in-fintech/
Recent Posts
December, 2021
For running a business safely and securely in the cloud, you have to comply with a certain set of rules. This set of rules or policies that govern your business in the cloud environment are referred to as cloud governance. Typically, these policies share many similarities with those governing on-premise IT infrastructures.
These rules are focused on enhancing privacy, data security, and managing risks in order to secure the data and ensure the smooth operation of the application. In addition to enhancing and optimizing security and efficiency, cloud governance best practices also help economize a business’ finances by allowing it to do more with less usage of resources.
Is Changing Your Current Governance Strategy Necessary?
Since every IT business has governance protocols and strategies, you might be wondering: why must I change my existing governance framework? Is it inadequate to handle problems raised by shifting to a cloud environment?
Well, the shorter version of that answer is, Yes. That is because the traditional IT governance framework is based on using centralized tools custom-made for workers of specific departments. Although this approach is best suited for centralized tools, the cloud environment and its operations by nature are decentralized.
A cloud governance strategy allows for creating a standardized policy that can be followed by various employees and departments of the business irrespective of their roles or subdivisions.
This strategy enables every employee to share and be on an equal footing while working in the cloud environment. The cloud, like enterprise infrastructure, needs bodies that govern its environment and standardize its services and other shared infrastructure issues.
Five Pillars of Cloud Governance
The efficiency of cloud installation is definitely dependent upon the organization’s systems and procedures. However, they also impact the structure of their platform and its underlying architecture. Based on the following five pillars, one can effectively implement designs that ensure scalability.
Operational Excellence
This pillar focuses on your workload operating as desired, monitoring every process and system to yield higher business value and continuously improve them. To ensure that your workload runs effectively with governance principles, operations will have to be performed as per code, incremental development of applications, and continuous refinement of processes involved.
Reliability
Reliability focuses on ensuring that your application performs as desired and that it does so continually without encountering a complete failure. Even the most reliable applications encounter failures, but they can recover quickly to meet customer demand. This is because their workloads are distributed, and the only resources they utilize are the ones that are required for production workloads.
Performance Efficiency
Performance efficiency is all about using technical resources efficiently for increasing business returns and operational efficiency. An example of such can be the usage of serverless platforms for app deployment. You can also deploy your workload across a vast region so customers accessing it globally can experience quicker interaction.
Security
This fourth pillar focuses on protecting the confidential information, data, and systems of your business. It urges you to secure your applications by implementing strong identification protocols and access controls
Cost Optimization
The last focuses on optimizing and reducing the operational and up-front costs of cloud development for your business, along with a monitored and streamlined usage of resources. It recommends that you focus on core development activities while outsourcing all the ancillary services to a third-party vendor to reduce the time taken for development and corresponding costs.
To learn more about each pillar in detail, download our whitepaper here.
Cloud Security Governance Challenges
Following are some of the practical use cases of cloud governance strategies and how they help tackle governance challenges.
Safeguarding Against Eventualities
When a business avails cloud services from a vendor, it is the responsibility of the service provider to provide continuous and reliable services. It is also their responsibility to enhance said services. If the vendor’s service goes down, so will be the performance of the client. Having a proper cloud governance model in place helps avoid such situations.
Cost-Effectiveness
Cloud development is an extremely cost-effective approach to application making, and with the right governance policies in place, the business can reap huge profits. A well-optimized cloud governance model can run far more efficient financial analytics and yield an optimal way of automating these policies. It can also retain management reporting to help with cost management.
Data Security
Securing your data is one of the top priorities of any IT business, and a well-planned cloud strategy can secure you against hackers exploiting loopholes. Cloud governance policies and best practices dictate that you build a robust authenticating system to safeguard your confidential information. The reason behind such a strict rule is that cloud service providers such as AWS have many inherent security bugs.
At GoDgtl, we help businesses establish robust cloud governance frameworks for hybrid, cloud, and multi-cloud environments, enabling companies to maintain compliance, democratize data, and support collaboration.
Get in touch with our data modernization team to learn more about how we can help your company build a solid data governance framework.
Recent Posts
December, 2021
Security is one of the top priorities for any organization that relies on digital technologies. And when it comes to the cloud, having a well-thought-out security strategy is absolutely essential. While the on-prem IT infrastructure focuses primarily on perimeter security, the security parameters for a cloud framework vary vastly from the former, and they require a rather layered approach.
As a market leader in cloud solutions, Microsoft Azure offers many out-of-the-box comprehensive security features that ensure multi-layered security of workloads hosted on its platform. Microsoft Azure puts a primary focus on customer facing controls that can be used to customize and increase security of applications and services.
Azure offers services such as virtual computing, cloud storage, analytics, and a lot more. It is a faster, more agile, and reliable replacement or supplement for your On-premise servers.
How do Azure security features work?
Since Azure’s Cloud Security infrastructure works on a shared security model, ensuring security on the cloud platform is a shared responsibility between Azure and the customer. In the case of on-prem solutions, customers bear the entire burden of ensuring security.
Here’s how the responsibility of different models is shared between Azure and customers:
- For IaaS, Azure ensures the security of networks, hosts, and data centers.
- For PaaS, along with what Azure ensures for IaaS, it also takes over the responsibility of ensuring the operating system’s security.
- For SaaS, along with what Azure ensures for PaaS, it also takes over the responsibility of ensuring the security for network controls, and applications.

While Azure takes up more responsibility for security from IaaS to SaaS, the onus of responsibility for the following three aspects falls on the customers:
- Data Governance and Rights Management
- Account and Access Management
- Endpoint Protection
How Microsoft Azure Ensures Your Organization’s Security
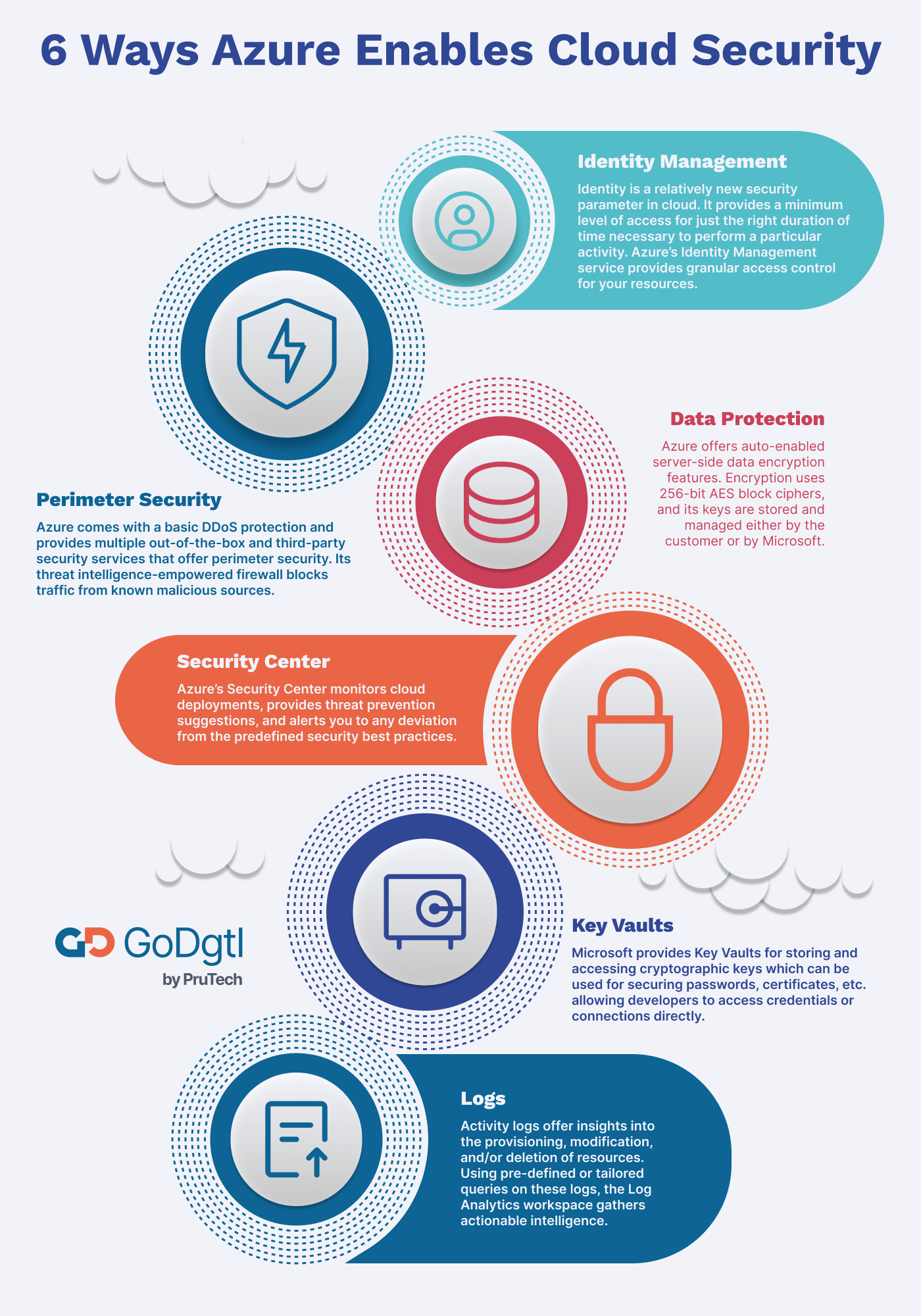
Here are the top six cloud security best practices that Microsoft Azure provides to enterprises for deploying workloads on their platform.
Identity Management
In the world of the cloud, identity is a relatively new security parameter. It provides a minimum level of access for just the right duration of time necessary to perform a particular activity. On the same operational principle of “least privilege,” Azure’s Identity Management service provides granular access control for your resources.
You can either make use of built-in roles that will define the access granted to a resource or custom-make roles as per the requirements of your organization. You should also make use of Azure’s Multi-Factor Authentication (MFA) for an additional layer of security.
Perimeter Security
Azure provides multiple out-of-the-box and third-party security services that offer perimeter security. Its threat intelligence-empowered firewall blocks out any traffic coming from known malicious sources. By default, all Azure resources come with a basic DDoS protection plan.
Data Protection
Azure offers auto-enabled server-side data encryption features for most of its services. The encryption uses 256-bit AES block ciphers, and its keys are stored and managed either by the customer or by Microsoft, as per the business requirements.
Security Center
Azure’s Security Center continuously monitors cloud deployments, provides threat prevention suggestions, and alerts you to any deviation from the predefined security best practices. Since this service is integrated with Azure resources, it also reduces the company overheads.
Key Vaults
As mentioned above, Microsoft provides Key Vaults for storing and accessing your cryptographic keys. You can also use these vaults for securing passwords, certificates, etc. The vaults are so safe and secure that even Microsoft cannot extract the data stored inside. This service allows developers to access security credentials or DB connection strings to the code directly from Key Vault.
Logs
The activity logs can offer insights into the provisioning, modification, and/or deletion of resources. You can send the data from these activity logs to Azure’s tools like Event Hubs for further analysis. Using pre-defined or tailored queries on these logs, the Log Analytics workspace gathers actionable intelligence.
Based on this intel, the outcome can provide a security status of your environments. For user access patterns, Azure AD logs are also a very useful service. It flags any unusual behavior as a potentially compromised identity.
Move to a Secure Azure Cloud Environment with GoDgtl
At GoDgtl, we understand how cloud computing and the resulting benefits of flexibility, scalability, security, and agility can transform organizations. Through our alliances with AWS & Azure for cloud or multi-cloud solutions, we provide broad and extensive cloud platform capabilities to empower digital business transformation for our global clients.
Recent Posts
November, 2021