Security is one of the top priorities for any organization that relies on digital technologies. And when it comes to the cloud, having a well-thought-out security strategy is absolutely essential. While the on-prem IT infrastructure focuses primarily on perimeter security, the security parameters for a cloud framework vary vastly from the former, and they require a rather layered approach.
As a market leader in cloud solutions, Microsoft Azure offers many out-of-the-box comprehensive security features that ensure multi-layered security of workloads hosted on its platform. Microsoft Azure puts a primary focus on customer facing controls that can be used to customize and increase security of applications and services.
Azure offers services such as virtual computing, cloud storage, analytics, and a lot more. It is a faster, more agile, and reliable replacement or supplement for your On-premise servers.
How do Azure security features work?
Since Azure’s Cloud Security infrastructure works on a shared security model, ensuring security on the cloud platform is a shared responsibility between Azure and the customer. In the case of on-prem solutions, customers bear the entire burden of ensuring security.
Here’s how the responsibility of different models is shared between Azure and customers:
- For IaaS, Azure ensures the security of networks, hosts, and data centers.
- For PaaS, along with what Azure ensures for IaaS, it also takes over the responsibility of ensuring the operating system’s security.
- For SaaS, along with what Azure ensures for PaaS, it also takes over the responsibility of ensuring the security for network controls, and applications.

While Azure takes up more responsibility for security from IaaS to SaaS, the onus of responsibility for the following three aspects falls on the customers:
- Data Governance and Rights Management
- Account and Access Management
- Endpoint Protection
How Microsoft Azure Ensures Your Organization’s Security
Here are the top six cloud security best practices that Microsoft Azure provides to enterprises for deploying workloads on their platform.
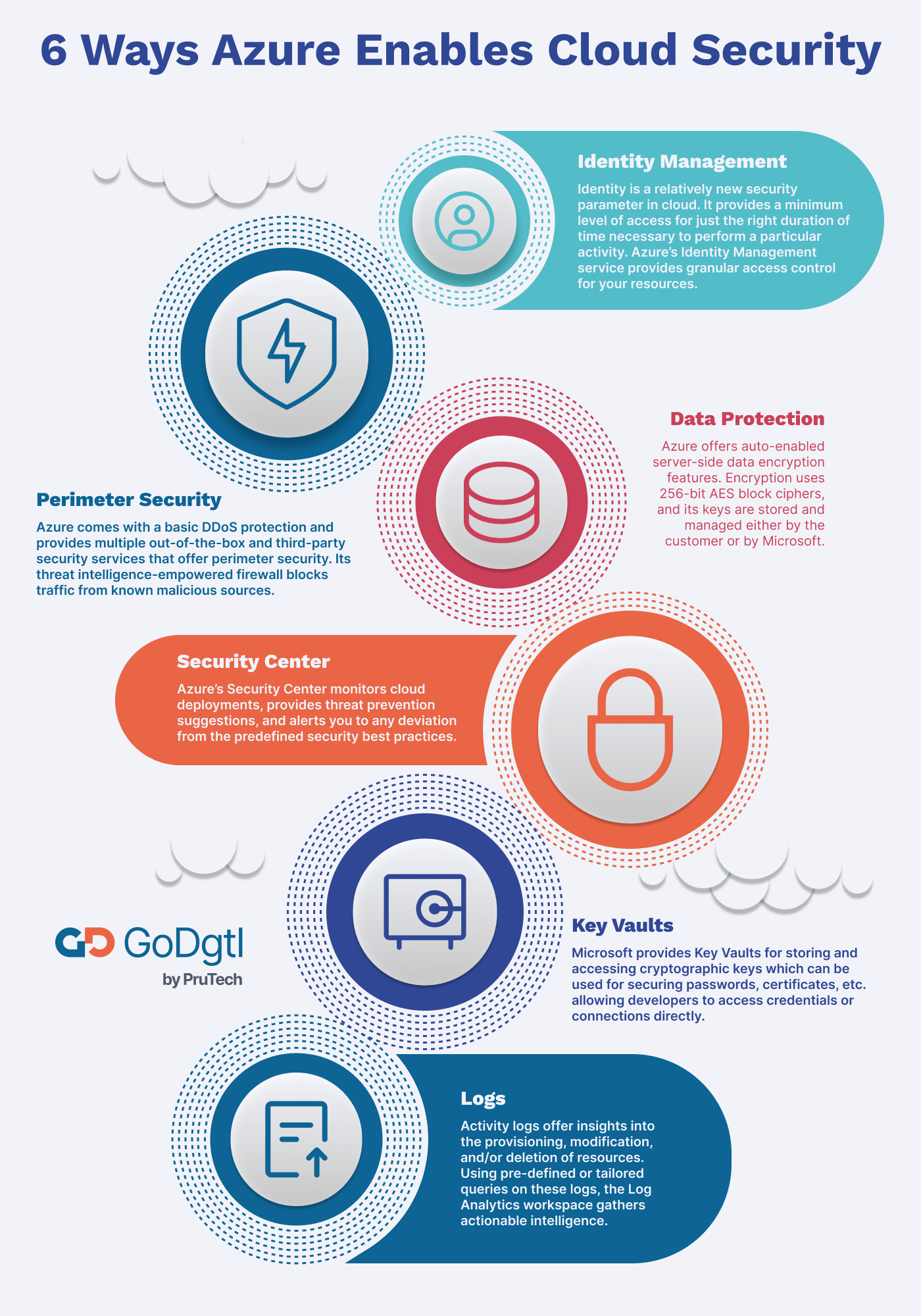
Identity Management
In the world of the cloud, identity is a relatively new security parameter. It provides a minimum level of access for just the right duration of time necessary to perform a particular activity. On the same operational principle of “least privilege,” Azure’s Identity Management service provides granular access control for your resources.
You can either make use of built-in roles that will define the access granted to a resource or custom-make roles as per the requirements of your organization. You should also make use of Azure’s Multi-Factor Authentication (MFA) for an additional layer of security.
Perimeter Security
Azure provides multiple out-of-the-box and third-party security services that offer perimeter security. Its threat intelligence-empowered firewall blocks out any traffic coming from known malicious sources. By default, all Azure resources come with a basic DDoS protection plan.
Data Protection
Azure offers auto-enabled server-side data encryption features for most of its services. The encryption uses 256-bit AES block ciphers, and its keys are stored and managed either by the customer or by Microsoft, as per the business requirements.
Security Center
Azure’s Security Center continuously monitors cloud deployments, provides threat prevention suggestions, and alerts you to any deviation from the predefined security best practices. Since this service is integrated with Azure resources, it also reduces the company overheads.
Key Vaults
As mentioned above, Microsoft provides Key Vaults for storing and accessing your cryptographic keys. You can also use these vaults for securing passwords, certificates, etc. The vaults are so safe and secure that even Microsoft cannot extract the data stored inside. This service allows developers to access security credentials or DB connection strings to the code directly from Key Vault.
Logs
The activity logs can offer insights into the provisioning, modification, and/or deletion of resources. You can send the data from these activity logs to Azure’s tools like Event Hubs for further analysis. Using pre-defined or tailored queries on these logs, the Log Analytics workspace gathers actionable intelligence.
Based on this intel, the outcome can provide a security status of your environments. For user access patterns, Azure AD logs are also a very useful service. It flags any unusual behavior as a potentially compromised identity.
Move to a Secure Azure Cloud Environment with GoDgtl
At GoDgtl, we understand how cloud computing and the resulting benefits of flexibility, scalability, security, and agility can transform organizations. Through our alliances with AWS & Azure for cloud or multi-cloud solutions, we provide broad and extensive cloud platform capabilities to empower digital business transformation for our global clients.
Recent Posts
Let's Talk
Our GoDgtl team is ready to help you!
We appreciate your interest in GoDgtl. Please select which team of experts you wish to engage: